1. LAN design model
1) LAN design principles
+Inspect the physical link
The bandwidth of the physical link is the basis of network design
+Analyze the characteristics of the data stream
Clarify the distribution characteristics of applications and data streams, so that resources can be distributed more effectively
For example, corporate mail service and workgroup shared printing have inconsistent network requirements
+Using a hierarchical model for design
The hierarchical structure can clearly interconnect multiple subnets, making the network easier to expand and manage
The hierarchy can be physical or logical
+ Consider network redundancy
A single point of failure in the network should not affect the interoperability of the network. The link load in the network should be properly balanced, which can be analyzed and designed according to the needs of different networks and the needs of different parts of the network
Applications and requirements drive changes at the network level
Core layer, convergence layer, access layer
Access layer:
The main function of the access layer is to provide network access for network users.
The access layer can further optimize specific user groups through access lists or filtering.
Specifically, the main functions of the access layer include: providing shared network bandwidth, providing switched network bandwidth, differentiated network segments, access control and data filtering based on the MAC layer (Layer 2).
The design goal of the access layer: low cost, highest possible user bandwidth, simple and convenient management.
Convergence layer:
The convergence layer is the dividing line between the access layer and the core layer, and it is the level that connects based on the strategy.
The main function of the convergence layer is to complete the definition of the network boundary. Its main functions include: VLAN aggregation, inter-VLAN routing, department or workgroup level access, broadcast domain or multicast domain definition, media conversion and message format conversion, and security control.
The design goals of the convergence layer: sufficient ports and bandwidth, three-layer and multi-layer switching characteristics, flexible and diverse business capabilities, necessary redundancy and load balancing.
Core layer:
The core layer is the data exchange center of the LAN, also known as the backbone of the LAN.
The main function of the core layer is to complete the exchange of data as quickly as possible, and should avoid deploying applications that affect the speed of data exchange in this layer.
The core layer design goals: sufficient ports and bandwidth, as strong as possible data exchange capacity, consider backup and load balancing.
From a specific implementation point of view, the core layer functions of small and medium-sized networks can be combined with the aggregation layer functions in one device; it is ideal for large-scale networks to be separated.
2) Example:
Network design requirements:
1. All information points have the ability to exchange;
2. Supports virtual network division and controlled access between departments;
3. The network is fault-tolerant and can carry out good network management;
4. Easy to expand and upgrade.
1). Access layer
The network design first needs to consider the physical link and service flow model.
The access layer is the level that provides access to network users, provides bandwidth, and restricts local traffic.
We must first classify the information points in the network:
1. The flow of ordinary hosts (PCs, workstations, etc.) follow the 80/20 model or the 20/80 model;
2. The company server needs to be frequently accessed by all ordinary hosts, and the department server is similar;
3. The vast majority of all information points are information points connected to ordinary hosts.
Construct an access layer switching network-access to ordinary hosts:
1. Using switched Ethernet technology to provide sufficient bandwidth for ordinary hosts, VLAN completes the function of isolating and limiting local traffic.
2. The marketing department and the technical department have a lot of information points. In order to reduce the impact of network broadcasting and conflicts, the internal work content of each department can be the same/similar, and the information points that need to frequently share data are grouped into a working group and arranged in the same VLAN in.
3. The administrative department and the financial department have a small number of information points, and it is also possible to no longer subdivide the working group and VLAN, but to use each department as a working group and assign a VLAN.
4. Use low-cost, high-port-density Ethernet switches for network equipment, and support network management.
2) Convergence layer
The convergence layer is the boundary between the core layer of the network and the access layer, and is a level based on policy connections; the convergence layer converges traffic and VLANs to provide department-level access.
Deploy the convergence layer
The finance department and the administration department have few access points, and the aggregation layer function can be directly deployed on the work group switch;
The marketing department and the technical department are divided into multiple working groups, and there are departmental servers, and the convergence layer network needs to be designed.
Build a convergence layer network
Adopt three-layer or multi-layer switching technology to provide VLAN aggregation and routing capabilities; provide 100M or Gigabit bandwidth for departmental servers; determine the uplink bandwidth according to the amount of traffic; design redundant links to connect to the core Layer to ensure the reliability of the network.
By dividing VLANs, users/hosts between different departments or work groups are isolated; on department-level tandem switches, through VLAN aggregation and inter-VLAN routing functions, these users/hosts can conditionally communicate and communicate with each other. access.
By deploying redundant links and STP protocols on the access and tandem switches, it can be ensured that network availability is still guaranteed when a certain tandem switch fails or a certain link fails. Similarly, in order to ensure the availability of departmental servers, it is also necessary to set up corresponding redundant links.
At the convergence layer, when connecting the server and the core layer switching equipment, the link bandwidth needs to be carefully determined according to the bandwidth required by the access user. When necessary, it is necessary to consider the technology of bundling multiple links to meet the bandwidth needs.
3) Core layer
The main consideration at the core layer of the network is to achieve fast data exchange. Therefore, in addition to link redundancy, the key consideration is the bandwidth of the physical link. Under feasible conditions, Gigabit Ethernet links should be deployed as much as possible.
The link redundancy of the core layer is very necessary, but you need to be cautious when considering the implementation of the STP protocol. The STP protocol requires a certain amount of convergent calculation time, and the response time to the failure of the link or node equipment will be relatively long-especially for the core layer. Here you can consider adopting a three-layer routing backup protocol to complete the management and switching functions of redundant links.
2. LAN design
1) Analysis of local area network requirements
In the early days, when network design engineers were designing local area networks, they had only limited equipment options, such as routers and hubs. Routers are often used as data flow centralized devices, that is, gateways; hubs are often used as the convergence point of hosts to connect to the router.
With the emergence of various new applications, such as video-on-demand, video conferencing, etc., more and more bandwidth is required, and Layer 2 switching technology has emerged, and the LAN design has undergone revolutionary changes. The Ethernet switch meets this requirement, it provides dedicated bandwidth for each port to perform wire-speed data forwarding. Ethernet switches replace hubs. In the third layer, routers are used to connect switched Ethernet networks to implement routing and forwarding, traffic management, and network security. The three-layer switching equipment has both the two-layer switching and the three-layer routing function at the same time.
1. Business analysis
+Funding budget
Protect user investment
Equipment purchase cost
Maintenance cost
+Enterprise Development Plan
Generally speaking, customers' requirements for LAN construction can be divided into business requirements and technical requirements.
In order to design a stable, efficient, and cost-effective LAN, first, you must carefully listen to the customer’s analysis of the company’s network conditions at this stage; if the customer has no knowledge of the network to be built, then, as a network design engineer, You should know the key issues that need to be considered in the construction of the customer's local area network, and guide customers to put forward their needs for the company's local area network.
On the premise of satisfying customers to design a safe, stable and efficient scalable network, choosing the most cost-effective network equipment and cables to reduce customer purchase costs is a primary issue; of course, for expansion projects on existing network facilities , How to protect the user’s current investment is also an indispensable consideration.
In the initial stage of network construction, the maintenance cost of the future network, the cost of WAN access, the salary of the administrator and the training cost, etc., are all customers and network designers must consider. Only in this way can we better evaluate the input-output ratio of network construction.
It may also face the following business needs raised by customers:
Due to the increase of corporate offices, in order to strengthen the management and operation of various departments and working groups, the local area network is required to realize the logical isolation of each functional group;
Due to the increase of corporate offices, in order to strengthen the management and operation of various departments and working groups, the local area network is required to realize the logical isolation of each functional group;
2. Technical analysis
(1) Physical topology analysis
+Enterprise physical topology problem
+Working Group Questions
+Cable line problem
First of all, you should understand the physical location of the customer's office area, the location of the building inside the office area, the characteristics of each floor, and the cable layout in the building to decide which network topology to choose. If it is to expand on the customer's existing network architecture, then it is time to consider which network topology architecture to choose on the basis of fully protecting the customer's investment.
Secondly, it is necessary to understand the composition of corporate network functional units, how many departments, how many work groups, how many project groups, and the distribution of these functional units from customers, in order to implement logical isolation of each functional unit, facilitate the management of the enterprise, and provide security Guaranteed.
Cable issues: When designing a network, physical cables are one of the most important issues to consider. Studies have shown that more than half of network failures are related to cable routing. It is necessary to analyze the distance limit of the cable, the strengths and weaknesses of different cable topologies, what type of cable is used in which network segment, and how to implement the overall structure of the cable line.
(2) Flow analysis
+workstation problem
+server problem
+Backbone network issues
+Multicast issues
+ Sudden data browsing problems
Server problem: Most computer networks nowadays are based on the Client/Server model. While we enjoy all the conveniences that this model brings, the server is often accessed by a large number of hosts, resulting in increased data traffic. In addition, server clustering has become a trend, and data centers are emerging. More and more companies place servers that support various applications to facilitate management and provide high-performance services. Because these centralized servers are required to provide services for the requests of multiple concurrent users at the same time, the bandwidth requirements of the terminal workstations of the servers are higher. Due to the needs of many emerging powerful applications, the requirement for dedicated bandwidth through switch ports and server access through high-performance backbone networks (such as Fast Ethernet, Gigabit Ethernet, etc.) are more urgent.
Backbone network issues: network hierarchical design models are becoming more and more popular. While we enjoy the many advantages that the network layered model brings to us, the core layer network equipment is bearing a great load brought about by various application requirements. We must consider increasing the bandwidth of the trunk road, selecting high-performance network equipment, improving network reliability, and realizing mutual backup and load sharing of core layer network equipment.
Multicast issues: Nowadays, applications based on multicast are becoming more and more widespread, such as VOD, video conferencing and other applications have emerged, these applications are bound to consume a lot of bandwidth. When applying multicast, it is necessary to consider the multicast performance of switches and routers, select multicast routing protocols and implement multicast strategies.
Sudden data traffic problem: After all, bandwidth resources are also limited. Sudden data traffic may cause large delays in network equipment and affect network performance. For delay-sensitive data traffic (for example: voice, video, etc.), implement QoS (Quality of Service) technology, and assign higher priority to these data traffic to ensure priority.
(3) LAN technology analysis
+The problem of LAN technology selection
+Standard compatibility issues
+Security issues
Technology choices: There are many kinds of LAN technologies, such as Layer 2 switching, Layer 3 switching, Fast Ethernet, Gigabit Ethernet, Virtual LAN, etc. Implement virtual local area network, implement multi-layer switching, deploy Fast Ethernet and Gigabit Ethernet by selecting the corresponding technology.
Standard compatibility: For a new network built on the existing network architecture, there may be various protocols in the original network, such as Novell's IPX/SPX protocol, IBM's SNA protocol, Apple's AppleTalk protocol, etc. These networks based on corporate standards are compatible with the TCP/IP protocol, or migrate to the TCP/IP protocol, and complete the wide-area interconnection between corporate networks. After all, TCP/IP is a de facto standard and has been widely available.
Security: LAN security can be divided into LAN internal access security and LAN wide area access security. According to statistics, 80% of illegal attacks on enterprise networks come from inside the enterprise network. Therefore, while preventing illegal access from outside, we should pay more attention to illegal attacks by internal employees. At this time, you should consider implementing a layered network architecture, deploying access control lists, implementing logical isolation of work groups, implementing software security features, and so on. In short, there are many ways to prevent illegal access, and you need to consider combining these technologies to provide maximum security for the local area network.
(4) Other technical issues
+Device selection problem
+Scalability issues
+Management and maintenance issues
Equipment selection: Under the premise of ensuring equipment availability, selecting the best network equipment can solve the technical defects that may exist in the network, such as network congestion and delay.
Scalability issues: The scale of enterprises is rapidly expanding, and various application requirements continue to emerge. It is necessary to consider designing a network that meets the future needs of enterprises.
Management issues: For the construction of local area networks, the distribution of network management workstations, and the selection of network management software must also be considered. At the same time, the management issues that may be brought about by future network growth must also be considered.
Network management can generally be divided into centralized management and distributed management.
In the centralized management network, all network management hosts are distributed at the same point. SNMP and RMON data polls the network management host from each remote node through MIB (Management Information Base), and analyzes it in a centralized location. The centralized management method is relatively simple and easy to implement, but it will be more difficult to implement centralized management for very large networks.
In the distributed management network, a large number of SNMP and RMON management data streams remain localized, and the local SNMP and RMON hosts are used for analysis and processing. However, a large number of distributed networks may bring high management costs.
After careful analysis of the network management system, centralized management or distributed management can be implemented, or the two management modes can be mixed.
(5) Comprehensive analysis
The needs of customers are diverse and network technologies are changing with each passing day. Therefore, there is no uniform network design plan to follow for the construction of local area networks. Facing the above various business and technical requirements, we must provide the best solution.
None of the above questions can be discussed separately, and the answers to some questions may be contradictory. For example, in order to improve network performance and increase data packet forwarding speed, high-performance routers or Layer 3 switches are required, but at the same time, investment in network equipment is increased. Therefore, it is necessary to mix various requirements analysis to make a satisfactory answer to the LAN design scheme.



|
|
|
|
How far(long) the transmitter cover?
The transmission range depends on many factors. The true distance is based on the antenna installing height , antenna gain, using environment like building and other obstructions , sensitivity of the receiver, antenna of the receiver . Installing antenna more high and using in the countryside , the distance will much more far.
EXAMPLE 5W FM Transmitter use in the city and hometown:
I have a USA customer use 5W fm transmitter with GP antenna in his hometown ,and he test it with a car, it cover 10km(6.21mile).
I test the 5W fm transmitter with GP antenna in my hometown ,it cover about 2km(1.24mile).
I test the 5W fm transmitter with GP antenna in Guangzhou city ,it cover about only 300meter(984ft).
Below are the approximate range of different power FM Transmitters. ( The range is diameter )
0.1W ~ 5W FM Transmitter :100M ~1KM
5W ~15W FM Ttransmitter : 1KM ~ 3KM
15W ~ 80W FM Transmitter : 3KM ~10KM
80W ~500W FM Transmitter : 10KM ~30KM
500W ~1000W FM Transmitter : 30KM ~ 50KM
1KW ~ 2KW FM Transmitter : 50KM ~100KM
2KW ~5KW FM Transmitter : 100KM ~150KM
5KW ~10KW FM Transmitter : 150KM ~200KM
How to contact us for the transmitter?
Call me +8618078869184 OR
Email me [email protected]
1.How far you want to cover in diameter ?
2.How tall of you tower ?
3.Where are you from ?
And we will give you more professional advice.
About Us
FMUSER.ORG is a system integration company focusing on RF wireless transmission / studio video audio equipment / streaming and data processing .We are providing everything from advice and consultancy through rack integration to installation, commissioning and training.
We offer FM Transmitter, Analog TV Transmitter, Digital TV transmitter, VHF UHF Transmitter, Antennas, Coaxial Cable Connectors, STL, On Air Processing, Broadcast Products for the Studio, RF Signal Monitoring, RDS Encoders, Audio Processors and Remote Site Control Units, IPTV Products, Video / Audio Encoder / Decoder, designed to meet the needs of both large international broadcast networks and small private stations alike.
Our solution has FM Radio Station / Analog TV Station / Digital TV Station / Audio Video Studio Equipment / Studio Transmitter Link / Transmitter Telemetry System / Hotel TV System / IPTV Live Broadcasting / Streaming Live Broadcast / Video Conference / CATV Broadcasting system.
We are using advanced technology products for all the systems, because we know the high reliability and high performance are so important for the system and solution . At the same time we also have to make sure our products system with a very reasonable price.
We have customers of public and commercial broadcasters, telecom operators and regulation authorities , and we also offer solution and products to many hundreds of smaller, local and community broadcasters .
FMUSER.ORG has been exporting more than 15 years and have clients all over the world. With 13 years experience in this field ,we have a professional team to solve customer's all kinds of problems. We dedicated in supplying the extremely reasonable pricing of professional products & services. Contact email : [email protected]
Our Factory

We have modernization of the factory . You are welcome to visit our factory when you come to China.

At present , there are already 1095 customers around the world visited our Guangzhou Tianhe office . If you come to China , you are welcome to visit us .
At Fair

This is our participation in 2012 Global Sources Hong Kong Electronics Fair . Customers from all over the world finally have a chance to get together.
Where is Fmuser ?
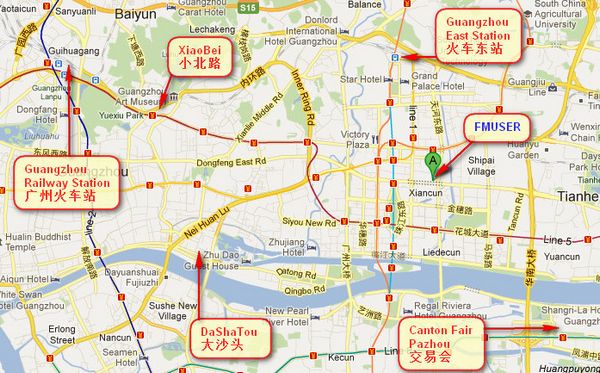
You can search this numbers " 23.127460034623816,113.33224654197693 " in google map , then you can find our fmuser office .
FMUSER Guangzhou office is in Tianhe District which is the center of the Canton . Very near to the Canton Fair , guangzhou railway station, xiaobei road and dashatou , only need 10 minutes if take TAXI . Welcome friends around the world to visit and negotiate .
Contact: Sky Blue
Cellphone: +8618078869184
WhatsApp: +8618078869184
Wechat: +8618078869184
E-mail: [email protected]
QQ: 727926717
Skype: sky198710021
Address: No.305 Room HuiLan Building No.273 Huanpu Road Guangzhou China Zip:510620
|
|
|
|
English: We accept all payments , such as PayPal, Credit Card, Western Union, Alipay, Money Bookers, T/T, LC, DP, DA, OA, Payoneer, If you have any question , please contact me [email protected] or WhatsApp +8618078869184
-
PayPal.  www.paypal.com www.paypal.com
We recommend you use Paypal to buy our items ,The Paypal is a secure way to buy on internet .
Every of our item list page bottom on top have a paypal logo to pay.
Credit Card.If you do not have paypal,but you have credit card,you also can click the Yellow PayPal button to pay with your credit card.
---------------------------------------------------------------------
But if you have not a credit card and not have a paypal account or difficult to got a paypal accout ,You can use the following:
Western Union.  www.westernunion.com www.westernunion.com
Pay by Western Union to me :
First name/Given name: Yingfeng
Last name/Surname/ Family name: Zhang
Full name: Yingfeng Zhang
Country: China
City: Guangzhou
|
---------------------------------------------------------------------
T/T . Pay by T/T (wire transfer/ Telegraphic Transfer/ Bank Transfer)
First BANK INFORMATION (COMPANY ACCOUNT):
SWIFT BIC: BKCHHKHHXXX
Bank name: BANK OF CHINA (HONG KONG) LIMITED, HONG KONG
Bank Address: BANK OF CHINA TOWER, 1 GARDEN ROAD, CENTRAL, HONG KONG
BANK CODE: 012
Account Name : FMUSER INTERNATIONAL GROUP LIMITED
Account NO. : 012-676-2-007855-0
---------------------------------------------------------------------
Second BANK INFORMATION (COMPANY ACCOUNT):
Beneficiary: Fmuser International Group Inc
Account Number: 44050158090900000337
Beneficiary's Bank: China Construction Bank Guangdong Branch
SWIFT Code: PCBCCNBJGDX
Address: NO.553 Tianhe Road, Guangzhou, Guangdong,Tianhe District, China
**Note: When you transfer money to our bank account, please DO NOT write anything in the remark area, otherwise we won't be able to receive the payment due to government policy on international trade business.
|
|
|
|
* It will be sent in 1-2 working days when payment clear.
* We will send it to your paypal address. If you want to change address, please send your correct address and phone number to my email [email protected]
* If the packages is below 2kg,we will be shipped via post airmail, it will take about 15-25days to your hand.
If the package is more than 2kg,we will ship via EMS , DHL , UPS, Fedex fast express delivery,it will take about 7~15days to your hand.
If the package more than 100kg , we will send via DHL or air freight. It will take about 3~7days to your hand.
All the packages are form China guangzhou.
* Package will be sent as a "gift" and declear as less as possible,buyer don't need to pay for "TAX".
* After ship, we will send you an E-mail and give you the tracking number.
|
|
|
For Warranty .
Contact US--->>Return the item to us--->>Receive and send another replace .
Name: Liu xiaoxia
Address: 305Fang HuiLanGe HuangPuDaDaoXi 273Hao TianHeQu Guangzhou China.
ZIP:510620
Phone: +8618078869184
Please return to this address and write your paypal address,name,problem on note: |
|