UDP is the abbreviation of User Datagram Protocol. The Chinese name is User Datagram Protocol. It is a connectionless transport layer protocol in the OSI reference model and provides transaction-oriented simple and unreliable information transmission services. It is the official specification of IETF RFC 768 which is UDP.
UDP protocol is the abbreviation of English UserDatagramProtocol, that is, user datagram protocol, which is mainly used to support network applications that need to transmit data between computers. Numerous client/server network applications including network video conferencing systems need to use the UDP protocol. The UDP protocol has been used for many years since its inception. Although its initial brilliance has been obscured by some similar protocols, even today, UDP is still a very practical and feasible network transport layer protocol.
Like the well-known TCP (Transmission Control Protocol) protocol, the UDP protocol is directly on top of the IP (Internet Protocol) protocol. According to the OSI (Open System Interconnection) reference model, UDP and TCP are both transport layer protocols.
The main function of the UDP protocol is to compress network data traffic into the form of datagrams. A typical datagram is a transmission unit of binary data. The first 8 bytes of each datagram are used to contain header information, and the remaining bytes are used to contain specific transmission data.
1. UDP header
The UDP header consists of 4 fields, each of which occupies 2 bytes, as follows:
1) Source port number
2) Target port number
3) Datagram length
4) Check value
The UDP protocol uses port numbers to reserve their own data transmission channels for different applications. UDP and TCP protocols use this mechanism to support multiple applications sending and receiving data at the same time. The data sender (can be client or server) sends UDP datagrams through the source port, and the data receiver receives the data through the destination port. Some network applications can only use static ports that are reserved or registered for them in advance; while other network applications can use unregistered dynamic ports. Because the UDP header uses two bytes to store the port number, the valid range of the port number is from 0 to 65535. Generally speaking, port numbers greater than 49151 represent dynamic ports.
The length of a datagram refers to the total number of bytes including the header and the data part. Because the length of the header is fixed, this field is mainly used to calculate the variable-length data part (also known as the data load). The maximum length of the datagram varies depending on the operating environment. Theoretically, the maximum length of a datagram including the header is 65535 bytes. However, some practical applications often limit the size of the datagram, sometimes reducing it to 8192 bytes.
The UDP protocol uses the check value in the header to ensure data security. The check value is first calculated by a special algorithm at the data sender, and needs to be recalculated after being transmitted to the receiver. If a datagram is tampered with by a third party during transmission or is damaged due to line noise or other reasons, the sender and receiver's check calculation value will not match, so the UDP protocol can detect whether there is an error. This is different from the TCP protocol, which requires a check value.
2. UDPvs.TCP
The main difference between UDP and TCP protocol is how to achieve reliable transmission of information. The TCP protocol contains a special delivery guarantee mechanism. When the data receiver receives the information from the sender, it will automatically send a confirmation message to the sender; the sender will continue to transmit other information only after receiving the confirmation message. Otherwise, it will wait until the confirmation message is received.
Unlike TCP, the UDP protocol does not provide a guarantee mechanism for data transmission. If the datagram is lost during the transmission from the sender to the receiver, the protocol itself cannot make any detections or prompts. Therefore, people usually call the UDP protocol an unreliable transmission protocol.
Compared with the TCP protocol, another difference of the UDP protocol is how to receive multiple datagrams that are unexpected. Unlike TCP, UDP does not guarantee the order of sending and receiving data. For example, an application on the client sends the following 4 datagrams to the server
D1
D22
D333
D4444
However, UDP may submit the received data to the server application in the following order:
D333
D1
D4444
D22
In fact, this disorder of UDP protocol basically rarely occurs, and usually only occurs when the network is very congested.
3. Application of UDP protocol
Some readers may ask, since UDP is an unreliable network protocol, what value or necessity is there? In fact, it is not. In some cases, the UDP protocol may become very useful. Because UDP has a speed advantage that TCP cannot match. Although various security functions are implanted in the TCP protocol, a large amount of system overhead will be occupied in the actual execution process, which will undoubtedly seriously affect the speed. On the other hand, UDP eliminates the reliable transmission mechanism of information and transfers functions such as security and sorting to upper-layer applications to complete, which greatly reduces the execution time and ensures the speed.
The earliest specification of the UDP protocol is RFC768, which was released in 1980. Although it has been a long time, the UDP protocol continues to play a role in mainstream applications. Many applications, including video teleconferencing systems, have proved the value of the UDP protocol. Because these applications pay more attention to actual performance than reliability, some reliability (for example, meeting quality) can often be sacrificed in order to obtain better use effects (for example, a higher frame refresh rate). This is the trade-off between UDP and TCP. According to different environments and characteristics, both transmission protocols will play a more important role in the future network world.
UDP protocol uses port numbers to reserve their own data transmission channels for different applications. UDP and TCP protocols use this mechanism to support multiple applications sending and receiving data at the same time. The data sender (can be client or server) sends UDP datagrams through the source port, and the data receiver receives the data through the destination port. Some network applications can only use static ports that are reserved or registered for them in advance; while other network applications can use unregistered dynamic ports. Because the UDP header uses two bytes to store the port number, the valid range of the port number is from 0 to 65535. Generally speaking, port numbers greater than 49151 represent dynamic ports.
The length of a datagram refers to the total number of bytes including the header and the data part. Because the length of the header is fixed, this field is mainly used to calculate the variable-length data part (also known as the data load). The maximum length of the datagram varies depending on the operating environment. Theoretically, the maximum length of a datagram including the header is 65535 bytes. However, some practical applications often limit the size of the datagram, sometimes reducing it to 8192 bytes.
UDP protocol uses the check value in the header to ensure data security. The check value is first calculated by a special algorithm at the data sender, and needs to be recalculated after being transmitted to the receiver. If a datagram is tampered with by a third party during transmission or is damaged due to line noise or other reasons, the sender and receiver's check calculation value will not match, so the UDP protocol can detect whether there is an error. This is different from the TCP protocol, which requires a check value.
Many link layer protocols provide error checking, including the popular Ethernet protocol. You may wonder why UDP also provides checksums. The reason is that the protocols below the link layer may not provide error detection in some channels between the source and the terminal. Although UDP provides error detection, when an error is detected, UDP does not perform error correction. It simply throws away the damaged message segment or provides warning information to the application.
4. Several features of UDP protocol
(1) UDP is a connectionless protocol. The source and terminal do not establish a connection before transmitting data. When it wants to transmit, it simply grabs the data from the application and throws it on the network as quickly as possible. On the sending end, the speed of UDP transmission of data is only limited by the speed at which the application generates data, the capacity of the computer, and the transmission bandwidth; on the receiving end, UDP puts each message segment in the queue, and the application removes it from the queue every time Read a message segment.
(2) Since the data transmission does not establish a connection, there is no need to maintain the connection status, including the receiving and sending status, so a server can transmit the same message to multiple clients at the same time.
(3) The header of the UDP packet is very short, only 8 bytes, which is very small compared to the 20-byte packet of TCP.
(4) Throughput is not regulated by the congestion control algorithm, but is only limited by the data rate of the application software, the transmission bandwidth, and the performance of the source and terminal hosts.
(5) UDP uses best effort delivery, that is, reliable delivery is not guaranteed, so the host does not need to maintain a complicated link state table (there are many parameters).
(6) UDP is message-oriented. The UDP of the sender delivers the message delivered by the application program down to the IP layer after adding the header. It neither splits nor merges, but preserves the boundaries of these messages. Therefore, the application needs to select the appropriate message size.
Although UDP is an unreliable protocol, it is an ideal protocol for distributing information. For example, reporting the stock market on the screen, displaying aviation information on the screen, and so on. UDP is also used in routing information protocol RIP (Routing Information Protocol) to modify the routing table. In these applications, if a message is lost, another new message will replace it after a few seconds. UDP is widely used in multimedia applications. For example, the RealAudio software developed by Progressive Networks is a software that transmits pre-recorded or live music to the client in real time on the Internet. The software uses RealAudio audio-on-demand. The protocol protocol is a protocol that runs on UDP, and most Internet telephony software products also run on UDP.
UDP = uridine diphosphate, a pyrimidine nucleotide, composed of bases, uracil and ribose, is mainly used as a raw material for RNA synthesis (transcription). In addition, UDP is also a product of DTP energy consumption. Its function is similar to ADP, but it is less common than ADP. Participate in the synthesis of microbial peptidoglycans.



|
|
|
|
How far(long) the transmitter cover?
The transmission range depends on many factors. The true distance is based on the antenna installing height , antenna gain, using environment like building and other obstructions , sensitivity of the receiver, antenna of the receiver . Installing antenna more high and using in the countryside , the distance will much more far.
EXAMPLE 5W FM Transmitter use in the city and hometown:
I have a USA customer use 5W fm transmitter with GP antenna in his hometown ,and he test it with a car, it cover 10km(6.21mile).
I test the 5W fm transmitter with GP antenna in my hometown ,it cover about 2km(1.24mile).
I test the 5W fm transmitter with GP antenna in Guangzhou city ,it cover about only 300meter(984ft).
Below are the approximate range of different power FM Transmitters. ( The range is diameter )
0.1W ~ 5W FM Transmitter :100M ~1KM
5W ~15W FM Ttransmitter : 1KM ~ 3KM
15W ~ 80W FM Transmitter : 3KM ~10KM
80W ~500W FM Transmitter : 10KM ~30KM
500W ~1000W FM Transmitter : 30KM ~ 50KM
1KW ~ 2KW FM Transmitter : 50KM ~100KM
2KW ~5KW FM Transmitter : 100KM ~150KM
5KW ~10KW FM Transmitter : 150KM ~200KM
How to contact us for the transmitter?
Call me +8618078869184 OR
Email me [email protected]
1.How far you want to cover in diameter ?
2.How tall of you tower ?
3.Where are you from ?
And we will give you more professional advice.
About Us
FMUSER.ORG is a system integration company focusing on RF wireless transmission / studio video audio equipment / streaming and data processing .We are providing everything from advice and consultancy through rack integration to installation, commissioning and training.
We offer FM Transmitter, Analog TV Transmitter, Digital TV transmitter, VHF UHF Transmitter, Antennas, Coaxial Cable Connectors, STL, On Air Processing, Broadcast Products for the Studio, RF Signal Monitoring, RDS Encoders, Audio Processors and Remote Site Control Units, IPTV Products, Video / Audio Encoder / Decoder, designed to meet the needs of both large international broadcast networks and small private stations alike.
Our solution has FM Radio Station / Analog TV Station / Digital TV Station / Audio Video Studio Equipment / Studio Transmitter Link / Transmitter Telemetry System / Hotel TV System / IPTV Live Broadcasting / Streaming Live Broadcast / Video Conference / CATV Broadcasting system.
We are using advanced technology products for all the systems, because we know the high reliability and high performance are so important for the system and solution . At the same time we also have to make sure our products system with a very reasonable price.
We have customers of public and commercial broadcasters, telecom operators and regulation authorities , and we also offer solution and products to many hundreds of smaller, local and community broadcasters .
FMUSER.ORG has been exporting more than 15 years and have clients all over the world. With 13 years experience in this field ,we have a professional team to solve customer's all kinds of problems. We dedicated in supplying the extremely reasonable pricing of professional products & services. Contact email : [email protected]
Our Factory

We have modernization of the factory . You are welcome to visit our factory when you come to China.

At present , there are already 1095 customers around the world visited our Guangzhou Tianhe office . If you come to China , you are welcome to visit us .
At Fair

This is our participation in 2012 Global Sources Hong Kong Electronics Fair . Customers from all over the world finally have a chance to get together.
Where is Fmuser ?
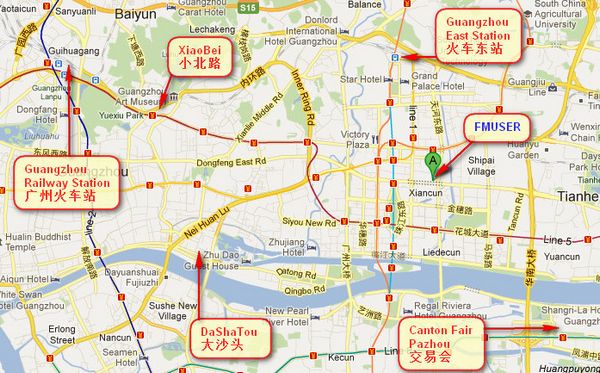
You can search this numbers " 23.127460034623816,113.33224654197693 " in google map , then you can find our fmuser office .
FMUSER Guangzhou office is in Tianhe District which is the center of the Canton . Very near to the Canton Fair , guangzhou railway station, xiaobei road and dashatou , only need 10 minutes if take TAXI . Welcome friends around the world to visit and negotiate .
Contact: Sky Blue
Cellphone: +8618078869184
WhatsApp: +8618078869184
Wechat: +8618078869184
E-mail: [email protected]
QQ: 727926717
Skype: sky198710021
Address: No.305 Room HuiLan Building No.273 Huanpu Road Guangzhou China Zip:510620
|
|
|
|
English: We accept all payments , such as PayPal, Credit Card, Western Union, Alipay, Money Bookers, T/T, LC, DP, DA, OA, Payoneer, If you have any question , please contact me [email protected] or WhatsApp +8618078869184
-
PayPal.  www.paypal.com www.paypal.com
We recommend you use Paypal to buy our items ,The Paypal is a secure way to buy on internet .
Every of our item list page bottom on top have a paypal logo to pay.
Credit Card.If you do not have paypal,but you have credit card,you also can click the Yellow PayPal button to pay with your credit card.
---------------------------------------------------------------------
But if you have not a credit card and not have a paypal account or difficult to got a paypal accout ,You can use the following:
Western Union.  www.westernunion.com www.westernunion.com
Pay by Western Union to me :
First name/Given name: Yingfeng
Last name/Surname/ Family name: Zhang
Full name: Yingfeng Zhang
Country: China
City: Guangzhou
|
---------------------------------------------------------------------
T/T . Pay by T/T (wire transfer/ Telegraphic Transfer/ Bank Transfer)
First BANK INFORMATION (COMPANY ACCOUNT):
SWIFT BIC: BKCHHKHHXXX
Bank name: BANK OF CHINA (HONG KONG) LIMITED, HONG KONG
Bank Address: BANK OF CHINA TOWER, 1 GARDEN ROAD, CENTRAL, HONG KONG
BANK CODE: 012
Account Name : FMUSER INTERNATIONAL GROUP LIMITED
Account NO. : 012-676-2-007855-0
---------------------------------------------------------------------
Second BANK INFORMATION (COMPANY ACCOUNT):
Beneficiary: Fmuser International Group Inc
Account Number: 44050158090900000337
Beneficiary's Bank: China Construction Bank Guangdong Branch
SWIFT Code: PCBCCNBJGDX
Address: NO.553 Tianhe Road, Guangzhou, Guangdong,Tianhe District, China
**Note: When you transfer money to our bank account, please DO NOT write anything in the remark area, otherwise we won't be able to receive the payment due to government policy on international trade business.
|
|
|
|
* It will be sent in 1-2 working days when payment clear.
* We will send it to your paypal address. If you want to change address, please send your correct address and phone number to my email [email protected]
* If the packages is below 2kg,we will be shipped via post airmail, it will take about 15-25days to your hand.
If the package is more than 2kg,we will ship via EMS , DHL , UPS, Fedex fast express delivery,it will take about 7~15days to your hand.
If the package more than 100kg , we will send via DHL or air freight. It will take about 3~7days to your hand.
All the packages are form China guangzhou.
* Package will be sent as a "gift" and declear as less as possible,buyer don't need to pay for "TAX".
* After ship, we will send you an E-mail and give you the tracking number.
|
|
|
For Warranty .
Contact US--->>Return the item to us--->>Receive and send another replace .
Name: Liu xiaoxia
Address: 305Fang HuiLanGe HuangPuDaDaoXi 273Hao TianHeQu Guangzhou China.
ZIP:510620
Phone: +8618078869184
Please return to this address and write your paypal address,name,problem on note: |
|